Here’s What You Need To Know About Access Control.


Access Control Systems offer the ability to regulate who is entering your facility. So how does that work?
Once a professional installation team has installed your access control system, the doors on site will automatically lock. This will allow only those who have the necessary credentials to gain entry. Administrators will assign each employee or resident a set of unique credentials. When presented to the reader, these credentials will allow the person access.
In this same way, an administrator can restrict access to a facility. Access control allows you the ability to restrict or grant accessibility. Prevent access to an ‘employee only’ entrance, lock down the lab or accounting offices in your warehouse or restrict access to sensitive information or private network rooms. These systems will alert you on unauthorized attempts to enter. This means that you will know when someone attempted to get access to the restricted area.

Access control systems are designed specifically to address a client’s particular security concerns, regardless of the size of the facility or number of people needing access. Schedules, set by administrators, are designed to fit a specific business hours or customized to include “after-hours” access, such as for a cleaning crew. Schedules can also be used to manage labor hours, ensuring only those employees slated to work that day or time have access to the building.
What Makes An Access Control System Work?
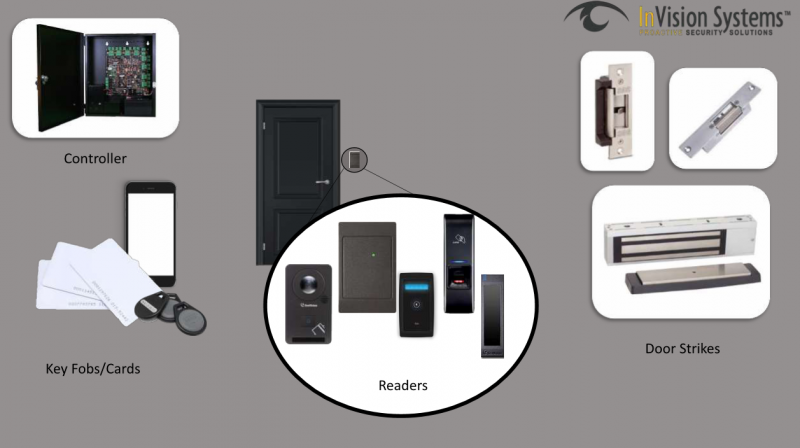
The components of the access control system include a door controller, electric door strikes and credential readers. In some cases, the facility may need a magnetic lock or other specialized hardware.
Controller
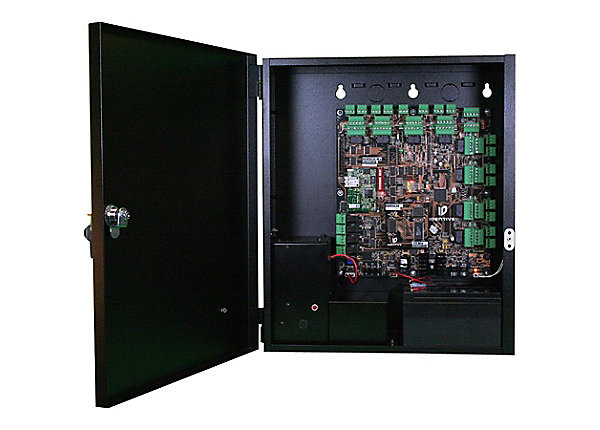
The door controller is exactly what it sounds like, it controls the doors connected to the access control system. This component is typically stored out of sight, in a network room or office. It is the brain of the system. When it receives a signal (within milliseconds) , it registers whether that credential is valid and then responds accordingly. The controller will either unlock the door or have the door remain locked.
The Readers
What component sends a signal to the controller? That’s the reader. A reader is a device installed, typically, on the outside of doors. It’s purpose is to identify valid credentials and send that information to the controller. There are many different types of readers, each used for a multitude of applications.
There are mullion readers, designed for aluminum door frames, standard key card/ fob readers which fit most applications, vandal resistant and PIN readers for extra security all the way to outdoor readers, long-range readers for vehicle traffic, bio-metric readers and highly encrypted readers.

So how do the readers know to send a signal to the door controller, telling it to unlock a door? By “reading” the authenticity of a credential. Usually presented as a unique code, a proximity key card, or a key fob. When a user presents the credential to the reader, within milliseconds, it is sending the information to the door controller.
Credentials

The controller reads the code, matches it to the system and sends a signal to the door strikes to unlock the door, if it determined that the credential was valid. With newer technology, you can use a smart phone, which houses the unique code or credential, to simply gain access without the need of a key card or fob. Key cards are similar to hotel key cards in look and function. Key fobs usually hook on a key ring and are harder to lose or damage than a key card.
All of these credentials use a frequency to communicate with the door controller. This sends unique binary codes which allow or restrict access. The lowest frequency is 125 KHz, this is somewhat older technology but still widely used today. When a user presents a credential to the reader, the internal chip of the key-card is powers up. It then sends it’s data to the reader. This is a unidirectional relationship, meaning that the flow of data is just one way. The credential to the controller. This standard transmission is very cost-effective.
The higher frequency cards, using 13.56MHz MIFARE, opt to store value in the key card/ fob. This grants an extra level of authentication.
The most secure readers use a bidirectional relationship between the credential and the reader. A bidirectional relationship means that the credential needs mutual authentication. It matches up an encrypted code presented from the credential to the encrypted code on the reader, think of it like a handshake. The credential reaches out to meet the hands of the reader, the reader grabs the hands of the credential, they agree that everything matches up, the door unlocks!
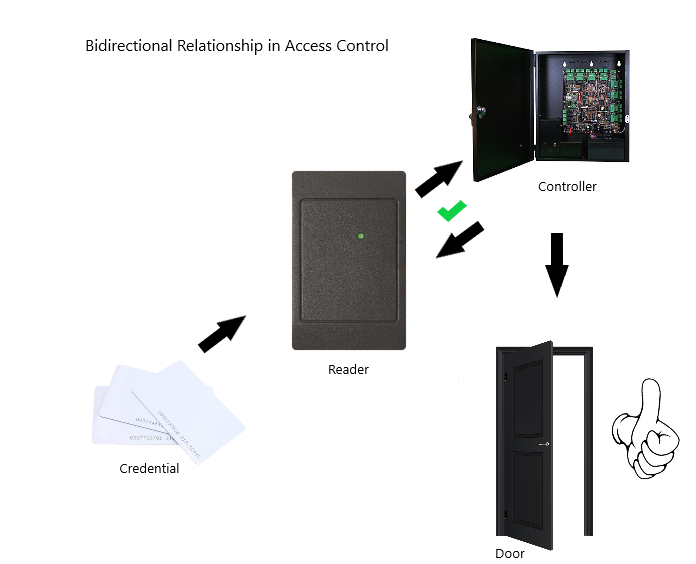
How Does The Controller Communicate With The Door?

This is where the door strikes come in. A door strike refers to the metal plate assembly installed in a door frame to catch the latch and hold the door closed. Just as with readers, there are all different types of door strikes used in a variety of settings. Typically, installers user electric door strikes for an Access Control system. The installation technician place the electric door strike in the mortise of the door frame or the ‘strike plate’ hole of the doors frame. The tech will then connect the electric door strike to a power supply and when activated it will release the latch to unlock the door.
These types of strikes keep the door locked from the outside . When closed behind someone, this strike automatically returns the door to the locked state. When someone wants to exit, they will use a ‘push to open’ bar or manual door handle to open the door from the inside. This is a Fail-Secure electric strike.
What Does This Mean?
A fail-secure lock will remain locked from the outside during a power outage when the electrical components of the system may not work. This keeps the property secure from outside intruders as the door will remain locked, even without power. The other side of this coin is the Fail-Safe door strikes. Mag-locks (or electromagnetic locks) are common fail-safe types of strikes. These strikes will unlock during a power outage, allowing free entry and exit. This type of strike is ideal for fire doors, glass doors included in an access control system or any opening where the exit must be controlled. They are also used with push bars, exit buttons or motion detector requests for exit devices.
The strike receives information from the controller. This lets the strike know that it is okay to release the latch, thereby unlocking the door. Access control components can work for ANY door. Solutions are tailored for any instance.
Here are some examples of how an Access Control Systems work:

Sally is given a key fob that is unique to her. She presents her key fob to the reader on the door she wishes to enter. If accepted, the door unlocks and she gains entry. If the key fob is fake or Sally does not present a fob to the reader, the door remains locked. No access will be given. It’s that simple!
Dave and Bob work at the same production facility. They both need access to the main employee entrance. Bob works on the production line and Dave works in the Lab. Production line employees are not permitted in the lab. An administrator customized Dave’s credentials to allow him access to the Lab and the main entrance. Bob’s key fob will only to allow him to get access to the main entrance. Dave and Bob’s key cards will both work to get access to the main entrance. However, only Dave’s fob will grant access to the lab. This is an extra layer of security for the lab. Additionally, an administrator could check the event logs and decide if Bob has attempted to get access to the lab. The access control software is designed to send notifications to the administrator of the system upon unauthorized attempts to enter.
Local Access Control vs Cloud Based Access Control
Local Access Control
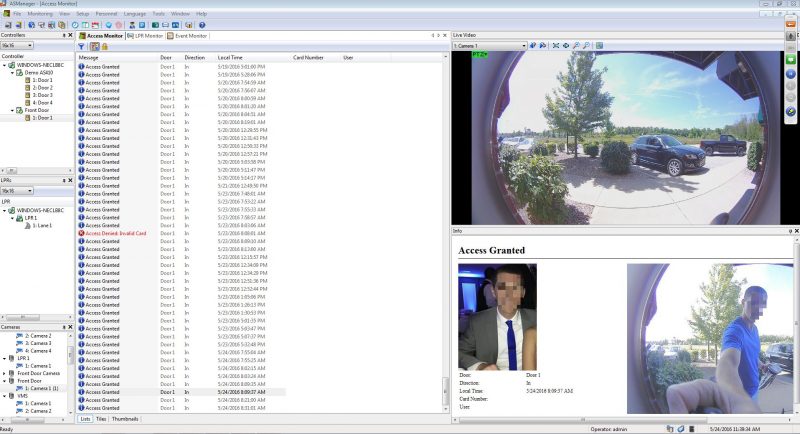
With an on-site system, you will need to have regular maintenance checks performed. You will want to make sure the system is up to date and running smoothly. The database for this system is stored locally. This means it can be vulnerable to data loss due to PC crash, hard-drive crash, power outages, etc.
There are typically no monthly fees associated with hosting the data locally on your PC on-site. Doing this cuts down on costs associated with the access control system. However, you may incur fees for maintaining the system.
Cloud Based Access Control
In today’s world, everything is moving to cloud based data storage for safeguarding information. Cloud based access control systems are no different and grant you the flexibility and greater functionality you need to effectively manage your site. Cloud based access control doesn’t require servers on-site or expensive computers to run the access control controllers. With all the software managed in the cloud, there are no costly license updates and no downtime for these updates. You will also eliminate your need for increased IT support. The customization goes beyond what you can do with users and schedules. Cloud based access control systems give you the option to add or remove extra features as they suit your needs.
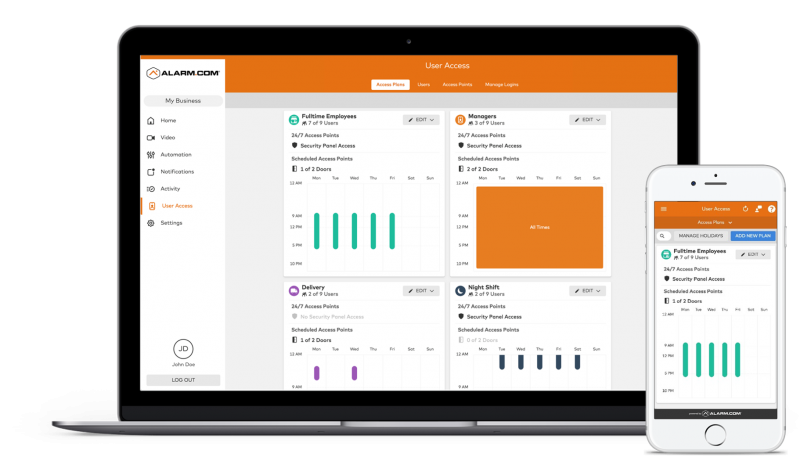
With a cloud-based access control system, administrators can manage the entire system remotely via mobile phone or PC. This includes adding and managing a specific user, customizing permissions for each user, setting schedules for access and even locking and unlocking doors to grant access.
What Are The Other Benefits Of Cloud Based Access Control?
- Flexibility-Manage one or many sites within your organization all from one device.
- No hard drives, software or servers to update, support or manage.
- Reduced Cost-Cloud Based systems run at a reduced cost to those with on-site IT managed servers.
- Customization-There are more features available with a cloud based system and these are easily added or removed to an account.
- Integration with other platforms such as with security cameras and burglar alarm systems.
Most of all, a Cloud-based Access Control system offers freedom from being tied down to a site while maintaining the integrity of your system.
How Will I know If Access Control Is Right For Me?
It doesn’t matter how many doors or how many people you need to manage, there is an access control solution for every application.
- Are unauthorized visitors a common occurrence?
- Do you have a whole building security plan in place that lacks access control?
- Have you ever found a customer wandering in an employee only area?
- Are there previous employees who may still have access to your building or sensitive areas within the facility?
- Need to limit access to network rooms, count rooms, managers offices, hazardous material storage rooms, high value assets, research labs, cashiers, parts/tools rooms or other areas that may need authorization to access?
- Would you like to limit access to sensitive documents or data that you store at your facility?
- Do you need to control who is entering your facility?
- Are there multiple employees accessing the building with no log or data on when or where they accessed the building?
- Are you changing the locks often?
- Do you need to restrict access to residents/staff/guests and vendors only?
Access Control Systems are used in multiple settings include:
- Office Buildings
- Warehouses
- Manufacturers
- Restaurants
- Retail Stores
- Government Facilities
- Educational Institutions
- Condo and Apartment Complexes
What’s Next For Access Control?
The future of Access Control is now. Access Control manufacturers and developers are leveraging new technologies everyday. Smartphone apps, readers that use facial recognition software and smarter systems,which allow you to integrate your security cameras or burglar alarms, are quickly becoming the norm.
Nearly everyone you know uses a smart phone. Many companies are swayed by the pervasive nature of smart phone technology. They are using smartphones as real key-cards for their access control systems. It’s easy to forget your key-card at home while rushing out of the door in the morning but not many people unknowingly forget their phones at home!
This technology has grown over the last several years and continues to propel forward. Access control manufacturers are continually developing specific applications to support supplanting a smart phone into a key-card. New advancements are slowly pushing traditional key cards and fobs to the wayside. Bio-metric readers also cut the need for a key fob or card.
Bio-metrics

Bio metric access control system components use fingerprints and voice or facial recognition software as credentials for access. Bio-metrics isn’t new to the access control game. However, with limits such as high cost, accuracy issues and privacy concerns bio-metric technology took a back seat to more accurate and secure forms of credentials. More recently, this technology has advanced due to the demand for ‘contactless entry’. This has made it more cost efficient, accurate and secure. Covid-19 has played a huge part in the need to limit exposure. Businesses want normalcy in their operations which has contributed to the growth we’ve seen in this specific industry.
Using these advancements in technology wouldn’t be possible without the growth of access control software . Systems are developing smarter brains and better analytics. At the forefront of this is the ability to integrate your systems. With platforms like Alarm.com (a central hub for managing your access control, camera systems and burglar alarms) leading the pack in seamless, straightforward integration you can bet more businesses and facilities will use this ability. But what does it all mean?

Integration

Big Bills Trucking has an alarm system, a camera system and an access control system. The owner uses three different management software applications to run each system. He has two dedicated PCs in the office to manage the camera system and the access control. The system, software and data used to run the systems are located on site.These systems aren’t integrated with each other. If an unauthorized user attempts to enter the building, Bill has to check the access control log, run another computer to check the camera feed and correspond the time of the video with the time of the unauthorized entry attempt. Big Bill does not have the time to pour through data for hours to find information about his event. When these systems are difficult to manage and time-consuming to deal with they aren’t providing you with ease and security of use.
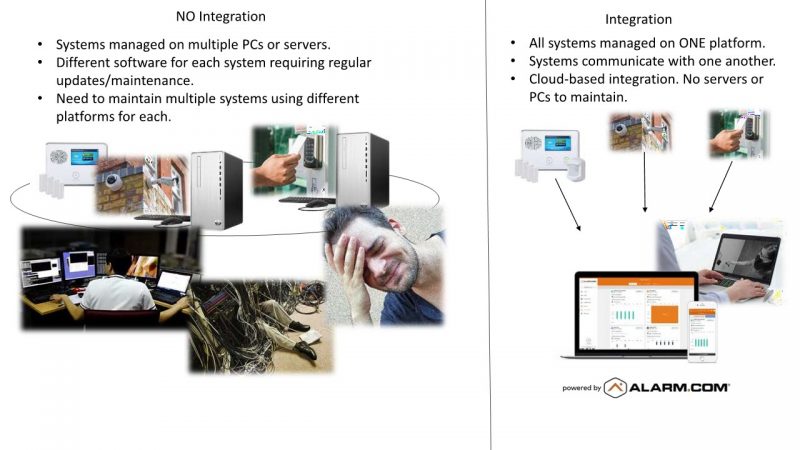
Nine times out of ten these systems sit in a dark room, running outdated software and collecting dust. Integration gives users the ability to manage their alarm, camera and access control systems on one application. Through one service, typically right on the phone or tablet customers can access their systems. Access control logs and video data are stored securely in the cloud. Because of this there is no need to have multiple PCs to run the systems. The cameras and alarm system work together with the access control to send alerts when an unauthorized user attempts to gain entry.
How Integration Works
The integrated systems allow administrators to see who attempted entry. You’ll learn the time the user attempted to enter and where the user attempted access. The systems support each other. When an event occurs, you will receive an alert or notification. After which, you’d log into the system directly from your mobile phone. Here, you will see everything you need to know about the event and almost immediately react.
Access Control Systems continue to develop new technologies. These systems manufacturers are dedicated to the security and functionality of the people who use these systems everyday. Access Control systems are becoming more popular for retail businesses, residential complexes, restaurants and schools. The systems being developed are less expensive, more user-friendly and most importantly, secure.
We understand that choosing the right technology card for your application can be confusing and somewhat complicated. We are here to help!
If you’re interested in learning more about how an access control system can benefit your business, we’d love to discuss it with you.
